Prodotti Certificati

Ortofrutta di Qualita'
CONOSCIAMOCI
Soc. Coop. Agricola La Reggia a.r.l.
La cooperativa La Reggia è nata nel 1985, dall’unione di piccoli e medi imprenditori agricoli, aderisce all’Organizzazione di Produttori AOA con la quale condivide l’attenzione alla sostenibilita’ ambientale.
L’azienda, situata nella provincia di Caserta, si estende su una superfice di circa 15 ettari investiti a serre ed è specializzata nella commercializzazione di ortofrutta da coltivazioni biologiche.


I NOSTRI PRODOTTI
What We Do

Ortaggi
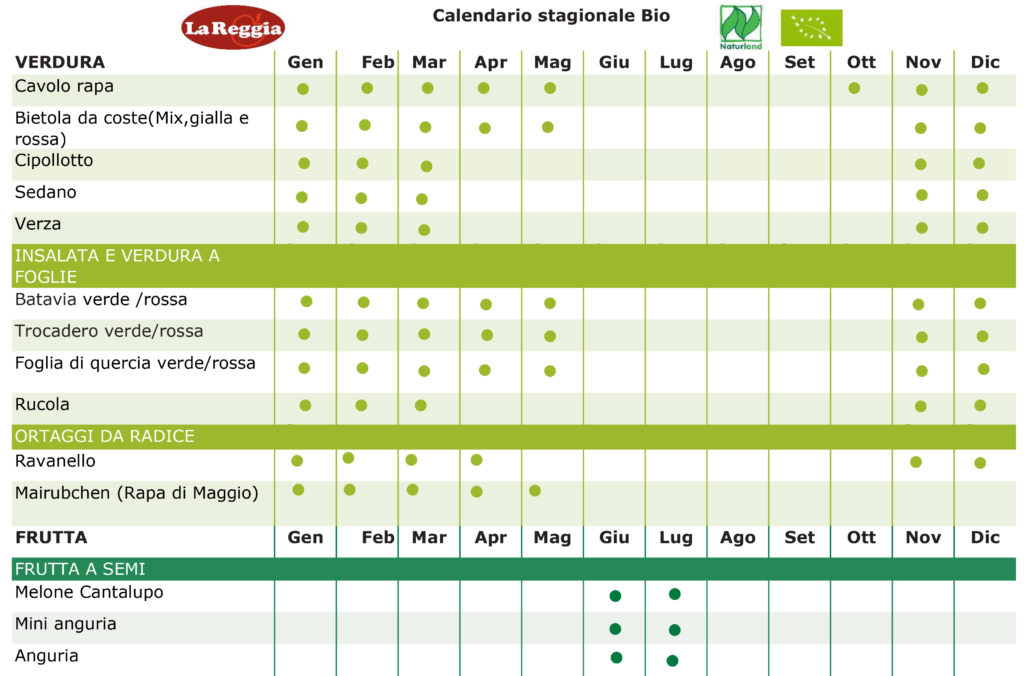
Produciamo e commercializziamo ortaggi bio di prima qualita'.

Frutta
Nel periodo estivo coltiviamo melone cantalupo e mini anguria.

L'Azienda
Raccogliamo prodotti freschi dal gusto intenso e squisito.
PRODOTTI FRESCHI
FRUTTA E VERDURA BIOLOGICA FRESCA DAL PRODUTTORE AL CONSUMATORE
Magazzino
Lo stabilimento si trova nel comune di S.Marcellino nella provincia di Caserta. Sono presenti i più moderni macchinari (lavatrice automatica, flow pack, imbustatrice, peso-prezzatrice e filmatrice). I prodotti pronti per la distribuzione, nazionale ed internazionale, vengono refrigerati in celle a temperatura controllata e poi caricati direttamente su automezzi refrigerati.
Certificazioni




L’azienda è specializzata nella commercializzazione di ortofrutta da coltivazioni biologiche, soggette al regime di controllo effettuato, da Bioagricert srl secondo il Reg. UE 834/07
I VANTAGGI
Why People Choose Us

ALWAYS FRESH!

100% ORGANIC

BEST QUALITY
Le nostre Ricette
Gnocco con il cavolo rapa
Sfiziosa ricetta preparato con l’impasto del cavolo rapa e condito con pesto di cavolo rapa.
Ingredienti:
Pesto cavolo rapa.
Aglio, olio di oliva, foglie di cavolo rapa, parmigiano e pinoli.